Our Daily Breach: Fool me twice
Murdoc takes a nostalgic trip to 2010 when he almost gets scammed by some guy in Montreal and yet still somehow ends up writing about Epsilon, again. I swear, he's not normally like this.

It's late September 2010, the radio is playing Rebecca Black's Friday on a Tuesday, so you turn that shit off immediately. You start up a Pandora mix and tab over to Reddit's r/adviceanimals where all the memes look the same.

You've got a few more minutes til your shift starts. You watch Gangnam Style one more time to see the view count tick up closer to one billion. In the end, you decide to go check your work inbox and get a headstart on the day.
You click an unread email from Marketbay.com offering a new copy of Adobe Reader for just $65. "Oh lit" you say to yourself because it's 2010 and people say dumb shit like this.
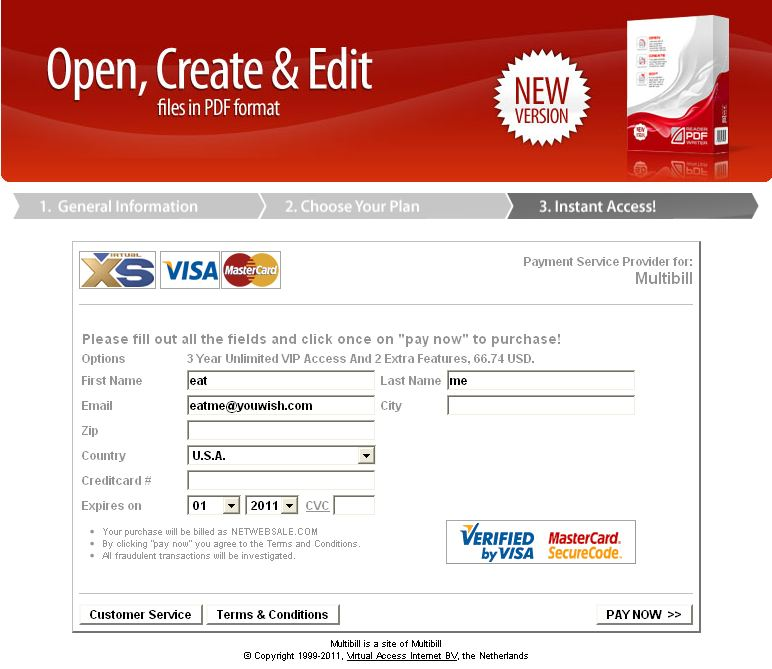
"Yaaas, this exactly what I need to open my PDF copies of The Girl With the Dragon Tattoo series" you say completely unaware of the horrors that lie within those books.
For once, the link to this software isn't malware. It's just a good ol' fashioned scam where you get absolutely nothing after paying for it.
For over three years, this scam would net the Montreal local David-Manuel Santos Da Silva and his two conspirators from the Netherlands approximately $2.5 million from sales generated by people clicking links on the spam emails. Fun fact, one Da Silva's accomplices was never caught and is still on the FBI most wanted list 14 years later.
Where did they get these emails in the first place? It would later come to light that nearly 1 billion emails were stolen from the Texas-based email marketing provider Epsilon. The brands impacted by the Epsilon breach include:
Capital One, JP Morgan Chase, US Bank, McKinsey Quarterly, Barclays, deviantArt, Kroger, McDonalds, City Market, Dillons, Jay C, Food 4 Less, Fred Meyer, Fry’s, King Soopers, Marriott Rewards, QFC, Ralphs, Ritz Carlton, Smith Brands, Walgreens, and even... The Home Shopping Network.
It might have been easier to here to name companies that were not in the Epsilon breach as it was considered the largest of its time.
In their statement to Brian Krebs in 2015, Epsilon management wrote:
“Epsilon confirms that it is among the victims of the cybercrime referenced in the Department of Justice’s indictment unsealed on March 5 against three individuals for their roles in hacking email service providers throughout the United States. We are pleased with the outcome of the investigation carried out by the U. S. Secret Service and the resulting indictment by the Department of Justice, and thank them for bringing this criminal activity to prosecution. Data protection is,and always has been, the top priority at Epsilon, and businesses and law enforcement must work together to prevent this type of criminal activity.”
Here's the real kicker to this story that I missed the first time I reported on Epsilon last year - as Epsilon management was writing this letter to Mr. Krebs touting how important data protection is to them, they had an executive and manager doing exactly what Da Silva and his accomplices were just sentenced for. The only difference really is that the inside actors Robert Reger & Dave Lytle would help scam more than 218,000 Americans out of more than $23.7 million. In total, it was a sum 10x more than Da Silva and his accomplices ever managed to grift using the same leaky data source, Epsilon.
Epsilon, if you're reading this, I've done some graphic work for you in my last article. Admittedly, I was a bit mean about it, I was still wrapping my head around the state of the cybersecurity industry as it did not match what I was educated on so I took it out on you. That wasn't entirely fair.
To make up for my snarkiness and for all you've done for the American people, I'd like to offer you my services to handle your written correspondence. I'll leave you with this sample to use when writting to future cybersecurity researchers reaching out for comment:
Data protection is, and always has been, a problem at Epsilon. We put "CONFIDENTIAL: DO NOT SHARE" right at top of all our spreadsheets full of everyone's contact info, but does anyone listen? NOOO! If you have any security suggestions please upload them to our SharePoint instance, the password is 'foolmetwice'."