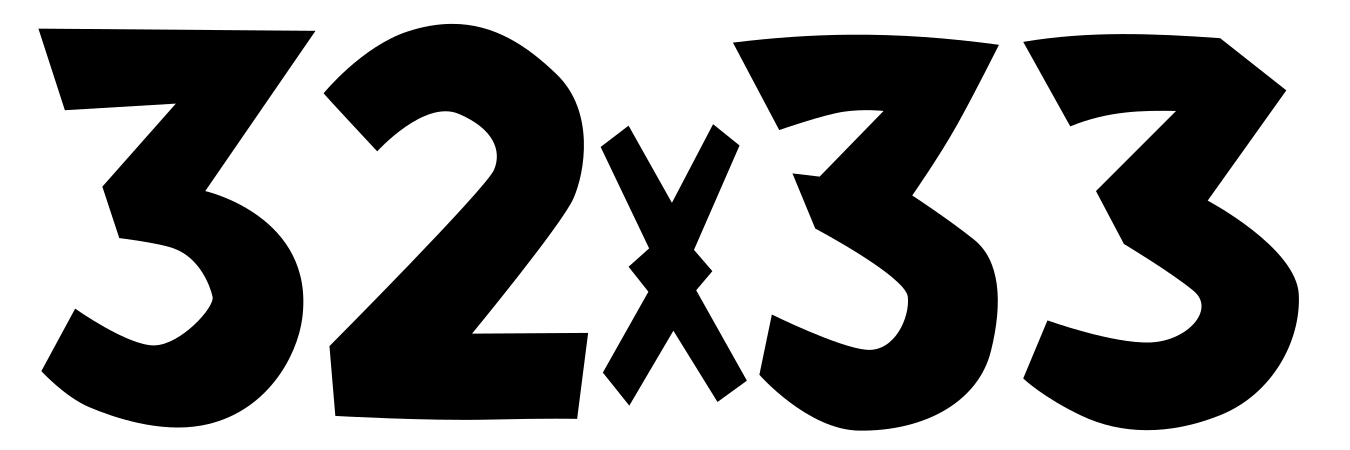beesknees
Post Incubation: part 2
Murdoc asks you a weird question, then shows some data & case studies that suggests Canadians aren't that clever. To solidify this, Murdoc openly shares his business idea and then puts his real email address in this article like a beaver tail eating fool.