Want to secure your enterprise? Don't buy enterprise security.
At this point, I'm not sure there is anything worse you can do to your security posture than pay for enterprise security solutions.

If you pay for cybersecurity services there is a very strong chance you are being scammed. Conned. Swindled.
Let's back up to the year 2024, when a short and bitter blog post on HackerNews with the title 'Cybersecurity is broken' made the front page. When I first read this post, I thought the author came across a bit hyperbolic at the time, but I don't anymore. Scarlett's words resonated with me (still do), so I joined her Discord community full of skeptics and meme slingers. Their harsh truths and gallows humor helped me figure out which vendors are worth their asking price. Turns out, almost none of them.
While it's easy to chalk it up to enshittification, there is more to it than unfettered corporate greed.
At NorthSec 2025 HD Moore, the creator of Metasploit, gave a talk entitled A Pirate's Guide to Snake Oil and Security to shed some light on how cybersecurity got into this state of charlatanism. While I fully recommend watching the full talk in its entirety (HD did his homework on this and the data is scathing), here's the short version:
Corporate sales got very, very good at their jobs - locking companies into 5+ year contracts with security products that can be easily onboarded but turn out to be an absolute pain to use & maintain.
Corporate law got very protective of disclosing their service performance and usability. In his talk, HD mentioned that most security vendors have a clause in their user agreement that prohibits you from sharing benchmarks or screenshots of their tools. As a result, there really isn't much data to compare security tools but let's take a look at what is available at vulnerability detection software:
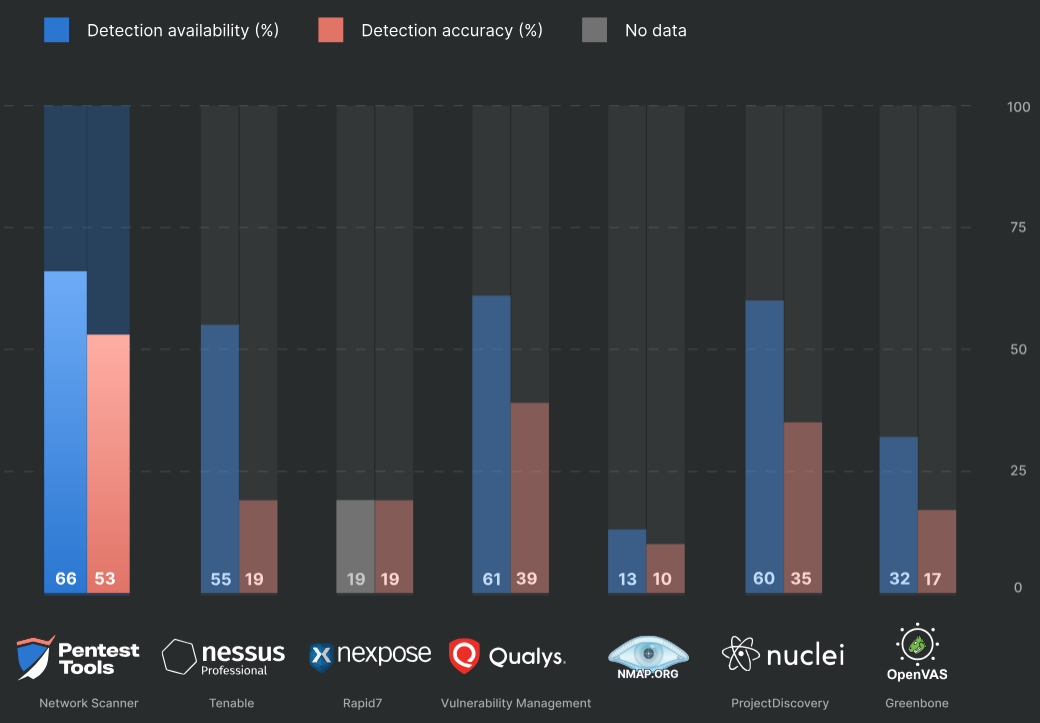
These sponsored results show that vulnerability tools miss most vulnerabilities and that detection accuracy is worse than a coin toss.
Don't worry, it gets worse! If you do decide to go with a well known security service provider, let's say a certain publicly traded company that made nearly 5 billion in gross profit the last 12 months, surely they don't have critical vulnerabilities in their software that would make attacks easier, right? Let's take a look at the top exploited vulnerabilities on the web right now:
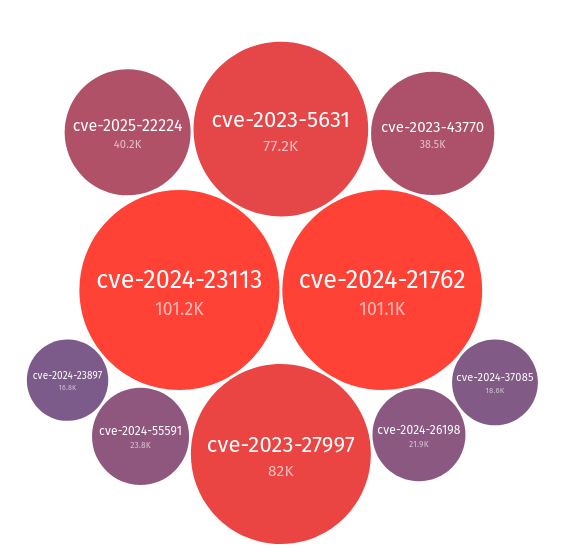
As of this writing, the top 3 exploited web vulnerabilities are exclusive to Fortinet FortiOS impacting almost 300K devices across the internet. It's important to note here, that this isn't a phase (mom!). In 2024 the top exploited vulnerabilities were:
- CVE-2024-3400, which allows command injection in the GlobalProtect feature of Palo Alto Networks PAN-OS.
- CVE-2023-46805 and CVE-2024-21887, which allow authentication bypass and command injection, respectively in the Ivanti Connect Secure VPN.
- CVE-2023-48788 is a SQL injection vulnerability in the FortiClient Endpoint Management Server.
Do you notice the common denominator here? Let me meme it out for you:

Okay that's just like one or two poorly managed companies right?
Sure, hypothetically let's just say it's only these big companies that are too big to fail and are just too slow publish security fixes, or bother investing in a shippable user experience.
We heard from the supplier side, but let's hear from the consumer side, perhaps the largest consumers of them all - the finance industry. Here's what JP Morgan's Chief Information Security Officer (CISO) Patrick Opet had to say about this in his open letter to third-party suppliers. He begins with:
The modern ‘software as a service’ (SaaS) delivery model is quietly enabling cyber attackers and – as its adoption grows – is creating a substantial vulnerability that is weakening the global economic system.
While it's pretty clear Mr. Oset used ChatGPT to write this letter (nice en dash bruh), he still drove the point home with how unsustainable this industry has become:
The pursuit of market share at the expense of security exposes entire customer ecosystems to significant risk and will result in an unsustainable situation for the economic system
This sentiment echoes what the Scarlett & the CrankySec community have been saying for years. The industry is spiraling into an unsustainable tailspin and leadership is maintaining status quo.
While I personally do not believe Mr. Oset's open letter will make any difference to the industry, it was still refreshing to read this take from a large financial institution.
The solution?
Buy local.
It's not just a good idea for your fruits & veggies, it's really the only viable path we have to take power away from the establishment. You might be surprised to find that smaller cybersecurity solutions are up and coming in your area, seek them out. Ask if they need advice or want help. Promote their shit on LinkedIn. Corporations spend all this money getting you to doom scroll and pay for their SEO-optimized landing page. You know what they would hate? You taking what little good ideas they once had and applying them at a smaller company that will take away from their precious market share. If you do it for nothing else, do it out of spite.
<3